Discover how NGate, a new Android malware, steals contactless payment data using NFC relay attacks. Learn about the latest cybersecurity threat target.







American chipmaker Microchip Technology Incorporated has disclosed that a cyberattack impacted its systems over the weekend, disrupting operations across multiple manufacturing facilities.
Headquartered in Chandler, Arizona, the company has roughly 123,000 customers across multiple industry sectors, including industrial, automotive, consumer, aerospace and defense, communications, and computing markets.
Due to an incident, some Microchip Technology manufacturing facilities operate at reduced capacity, affecting the company’s ability to meet orders. Microchip Technology also had to take steps to manage the situation, such as shutting down some systems and isolating the affected ones following the breach.

Ransomware victims have paid $459,800,000 to cybercriminals in the first half of 2024, setting the stage for a new record this year if ransom payments continue at this level.
Last year, ransomware payments reached a record $1.1 billion, which Chainalysis previously predicted from stats gathered in the first half of the year when ransomware activity grossed $449,100,000.
We now stand at approximately 2% higher than 2023’s record-breaking trajectory from the same period despite significant law enforcement operations that disrupted large ransomware-as-a-service operations, such as LockBit.
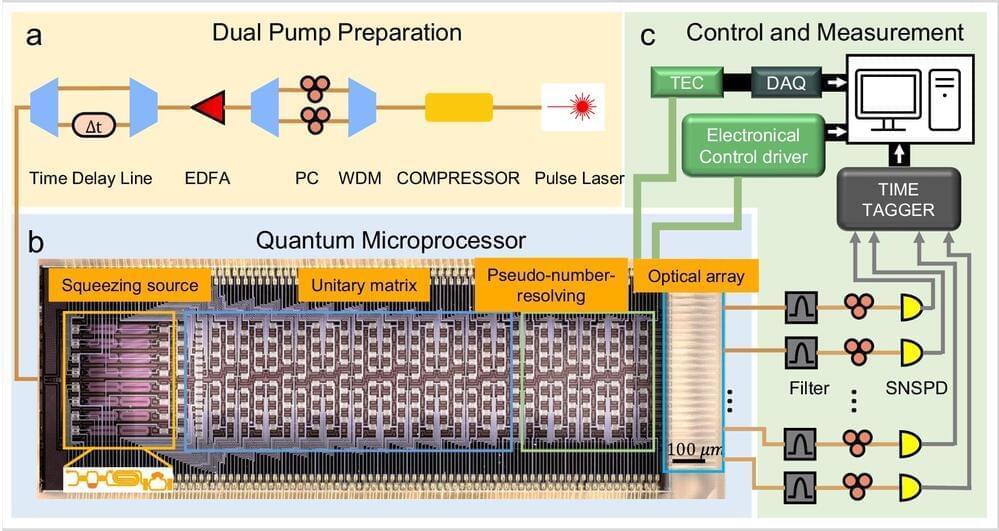
Quantum simulation enables scientists to simulate and study complex systems that are challenging or even impossible using classical computers across various fields, including financial modeling, cybersecurity, pharmaceutical discoveries, AI and machine learning. For instance, exploring molecular vibronic spectra is critical in understanding the molecular properties in molecular design and analysis.

RansomHub ransomware operators are now deploying new malware to disable Endpoint Detection and Response (EDR) security software in Bring Your Own Vulnerable Driver (BYOVD) attacks.
Named EDRKillShifter by Sophos security researchers who discovered it during a May 2024 ransomware investigation, the malware deploys a legitimate, vulnerable driver on targeted devices to escalate privileges, disable security solutions, and take control of the system.
This technique is very popular among various threat actors, ranging from financially motivated ransomware gangs to state-backed hacking groups.

Security experts are warning that a background check site may have been breached, resulting in the potential exposure of billions of Social Security and address records that could cover everyone in the United States.
As BleepingComputer reports, a hacking forum lit up when a user claimed to have access to a huge cache of documents gleaned from data brokerage National Public Data.
Though it doesn’t share its methodology on its website, NPD is believed to scrape its data from publicly available records to create individual user profiles generally used by private investigators or in background or criminal records checks.