Arid Viper launches mobile espionage campaign using trojanized Android apps to deliver AridSpy spyware, targeting Middle East users via fake messaging.


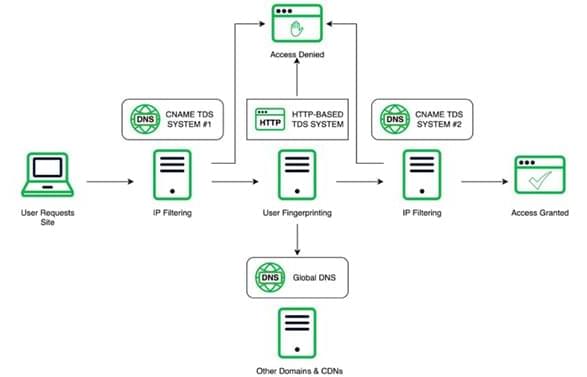
A Chinese organized crime syndicate with links to money laundering and human trafficking across Southeast Asia has been using an advanced “technology suite” that runs the whole cybercrime supply chain spectrum to spearhead its operations.
Infoblox is tracking the proprietor and maintainer under the moniker Vigorish Viper, noting that it’s developed by the Yabo Group (aka Yabo Sports), which has been linked to illegal gambling operations and pig butchering scams in the past. In late 2022, it rebranded as Kaiyun Sports and has since been absorbed into another newly formed entity called Ponymuah.
The suite, marketed in China as “baowang” (“包网,” meaning full package) encompasses several components such as Domain Name System (DNS) configurations, website hosting, payment mechanisms, advertising, and mobile apps. It also hosts thousands of domain names and numerous brands in an infrastructure that’s tied to Hong Kong and China.
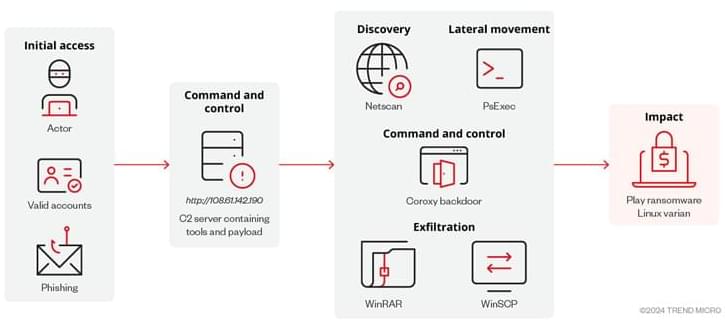


Computer security company CrowdStrike is linked to a major IT outage affecting banks, airports, supermarkets and businesses across Australia and the world.
Airport check-in systems across the globe have been disrupted and businesses have reported the “blue screen of death” and IT outages.
Follow our live blog or download the ABC News app and subscribe to our range of news alerts for the latest updates.


Related: High-G data recorder helps Air Force munitions testing
The Army wants a company to build and deliver MDAC prototypes using existing fielded and mature technologies. MDAC will be air-, rail-, and sea-transportable per MIL-STD-1366; will be able to move rapidly for survivability; have automated high rates of fire with HVP; and have emote weapon firing; have deep magazine capacity, rapid ammunition resupply, and high operational availability. Companies interested also will demonstrate supportability, safety, and cyber security.
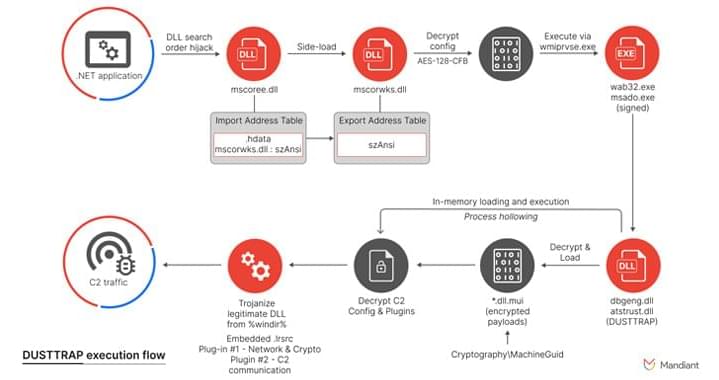
JAXA has not said who the attackers were, but most cybersecurity observers are pointing the finger at state actors working for China.
“The fact that a space agency was targeted with a sophisticated complex attack indicates a state actor with goals to compromise data, not just gather intelligence or send a political message, with the lead suspect being a China affiliated cyber security private company of some sort,” said Irina Tsukerman, a geopolitical analyst and the president of Scarab Rising, a global strategy advisory firm. “Such an attack is likely the work of either a state-backed independent hacker, possibly part of an intelligence gathering gang, whose methods could potentially be analyzed and compared to prior such attacks, or it could be attributed to a private cybersecurity company, most likely affiliated with China, in which case prior incidents could be harder to detect. The most interesting detail was the description of the attack and the fact that the attacker used several different types of malware and nevertheless went undetected.

The call and text message records from mid-to-late 2022 of tens of millions of AT&T cellphone customers and many non-AT&T customers were exposed in a massive data breach, the telecom company revealed Friday.
AT&T said the compromised data includes the telephone numbers of “nearly all” of its cellular customers and the customers of wireless providers that use its network between May 1, 2022 and October 31, 2022.
The stolen logs also contain a record of every number AT&T customers called or texted – including customers of other wireless networks – the number of times they interacted, and the call duration.