It’s moving towards a “single network future.”

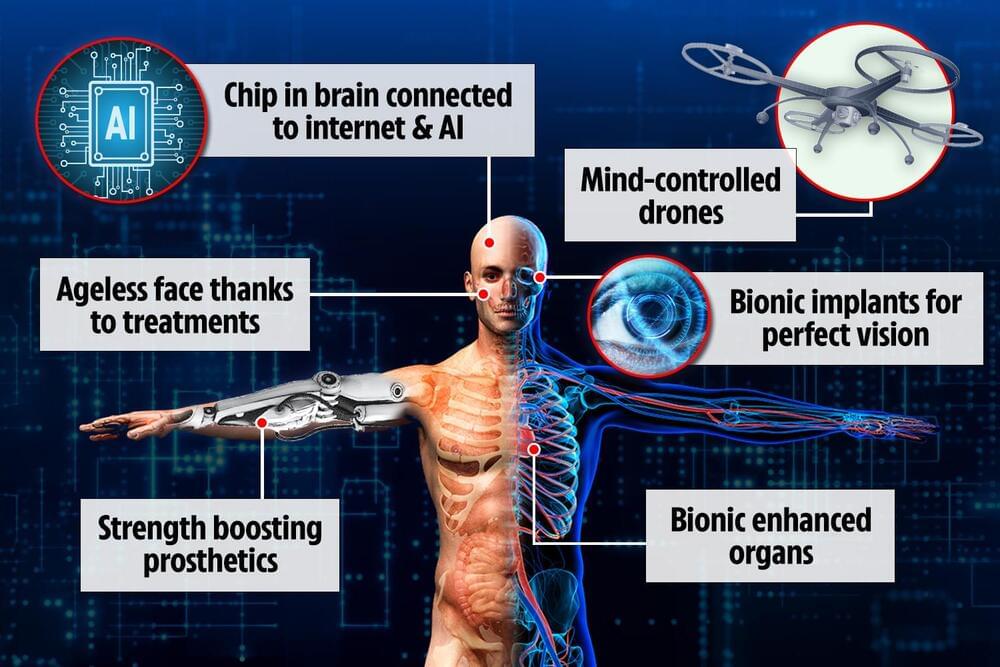
HUMANS in the next 100 years could be part-machine, part-flesh creatures with brain chips and bionic limbs and organs in a vision of “cyborgs” once described by Elon Musk.
Men and women born around 2100 could live in a world very different to ours as humans may be totally connected to the internet and meshed together with artificial intelligence.
Mobile phones would no longer be needed — as everything you now do with your smartphone will now be done with a chip in your brain.

It’s part of a South Korean project to develop one of the largest semiconductor manufacturing hubs in the world.
An investment of $230 billion is expected to be made in the next two decades by Samsung to further semiconductor manufacturing.
The mega cluster, which will feature five new semiconductor plants built by Samsung, will be set in the Gyeonggi Province and is expected to be completed by 2042.
Holgs/iStock.
The investment will be a part of a South Korean project to develop one of the largest semiconductor manufacturing hubs in the world, near its capital city of Seoul. Samsung leads in the production of memory chips, smartphones, and TVs in the world.
Chinese Phone blog dedicated to providing breaking news, expert reviews, Chinese Phones, Android Apps, Chinese Android Tablets and how tos.

Google announced a new open source program called Open Health Stack for developers to build health-related apps. These tools, unveiled at the company’s “The Check Up” special event this week, include a Software Developer Kit (SDK) for Android and design guidelines for health apps.
The search giant said that the stack is centered around the Fast Healthcare Interoperability Standards (FHIR) standards. This makes it easier for developers to capture the information and healthcare workers to access that. FHIR has been adopted by a lot of major electronic health record (EHR) providers.
The Open Health Stack gives developers access to Android FHIR SDK to build secure apps that can also work offline; a design guide to help developers make data capture easy; and FHIR Analytics to derive insights complex structure of the framework and FHIR Info Gateway to assign role-based access of data to various stakeholders. The last two components are available under early access, and Google is developing more features within both.
Things are moving at lightning speed in AI Land. On Friday, a software developer named Georgi Gerganov created a tool called “llama.cpp” that can run Meta’s new GPT-3-class AI large language model, LLaMA, locally on a Mac laptop. Soon thereafter, people worked out how to run LLaMA on Windows as well. Then someone showed it running on a Pixel 6 phone, and next came a Raspberry Pi (albeit running very slowly).
But let’s back up a minute, because we’re not quite there yet. (At least not today—as in literally today, March 13, 2023.) But what will arrive next week, no one knows.

Researchers at the School of Cyber Security at Korea University, Seoul, have presented a new covert channel attack named CASPER can leak data from air-gapped computers to a nearby smartphone at a rate of 20bits/sec.
The CASPER attack leverages the internal speakers inside the target computer as the data transmission channel to transmit high-frequency audio that the human ear cannot hear and convey binary or Morse code to a microphone up to 1.5m away.
The receiving microphone can be in a smartphone recording sound inside the attacker’s pocket or a laptop in the same room.
Reports say that the Nokia Magic Max will come in three different memory configurations. We will have 8GB, 12GB and 16GB of RAM with 256GB and 512GB storage options. It will launch with Android 13 out of the box with Snapdragon 8 Gen 2 SoC under the hood. We may also see a 6.7-inch AMOLED display with 120Hz refresh rate on the device. Corning Gorilla Glass 7 protection could be on the display of the upcoming flagship device from Nokia.
The device will feature a triple camera setup on the back with 144MP main sensor, 64MP ultrawide and 48MP Telephoto lens. Rumors have suggested a massive 7950mAh battery which can also charge from 0 to 100 within a few minutes, thanks to the 180W fast charger.
The memory configurations will determine the price of each variant. Nevertheless, sources have suggested the starting price to be around $550 (INR44,900). There is no firm rumor with respect to the launch date, but we expect to see the launch of the Nokia Magic Max in a matter of few weeks.
There’s an old magic trick known as the miser’s dream, where the magician appears to pull coins from thin air. Australian scientists say they can now generate electricity out of thin air with the help of some enzymes. The enzyme reacts to hydrogen in the atmosphere to generate a current.
They learned the trick from bacteria which are known to use hydrogen for fuel in inhospitable environments like Antarctica or in volcanic craters. Scientists knew hydrogen was involved but didn’t know how it worked until now.
The enzyme is very efficient and can even work on trace amounts of hydrogen. The enzyme can survive freezing and temperature up to 80 °C (176 °F). The paper seems more intent on the physical mechanisms involved, but you can tell the current generated is minuscule. We don’t expect to see air-powered cell phones anytime soon. Then again, you have to start somewhere, and who knows where this could lead?

FarmboxRx’s Ashley Tyrner told The New York Post Friday that “all panic broke loose” when she went to login to the company’s SVB account to get a transaction approved when the system crashed and locked her out.
“When I went to log in to approve the wire, the system was completely crashed,” Tyrner told the newspaper. “It would not let anybody in.”
Tyrner called customer service and her SVB personal banker who “wouldn’t answer” the phone. She said he later texted her to apologize and said the bank was attempting to fix the issue.