Archive for the ‘cybercrime/malcode’ category: Page 188
Oct 30, 2016
Google’s neural networks created their own encryption method
Posted by Karen Hurst in categories: cybercrime/malcode, encryption, information science, robotics/AI
Fortifying cybersecurity is on everyone’s mind after the massive DDoS attack from last week. However, it’s not an easy task as the number of hackers evolves the same as security. What if your machine can learn how to protect itself from prying eyes? Researchers from Google Brain, Google’s deep Learning project, has shown that neural networks can learn to create their own form of encryption.
According to a research paper, Martín Abadi and David Andersen assigned Google’s AI to work out how to use a simple encryption technique. Using machine learning, those machines could easily create their own form of encrypted message, though they didn’t learn specific cryptographic algorithms. Albeit, compared to the current human-designed system, that was pretty basic, but an interesting step for neural networks.
To find out whether artificial intelligence could learn to encrypt on its own or not, the Google Brain team built an encryption game with its three different entities: Alice, Bob and Eve, powered by deep learning neural networks. Alice’s task was to send an encrypted message to Bob, Bob’s task was to decode that message, and Eve’s job was to figure out how to eavesdrop and decode the message Alice sent herself.
Continue reading “Google’s neural networks created their own encryption method” »
Oct 25, 2016
Russian military build impenetrable closed internet – and mocks US technology
Posted by Karen Hurst in categories: cybercrime/malcode, internet, military
For my CISO/ CSO friends.
It is believed that Russia has the Internet that is considered as impenetrable. Such technology protects Russia from hacking attempts.
The World Wide Web (WWW) is prone to hacking, as shown in the recent cyber attacks on the US which led to outages on giants including Twitter, Amazon and Spotify, for which Russia has been largely blamed, so the Eastern European powerhouse has upped its security measures.
Continue reading “Russian military build impenetrable closed internet – and mocks US technology” »
Oct 24, 2016
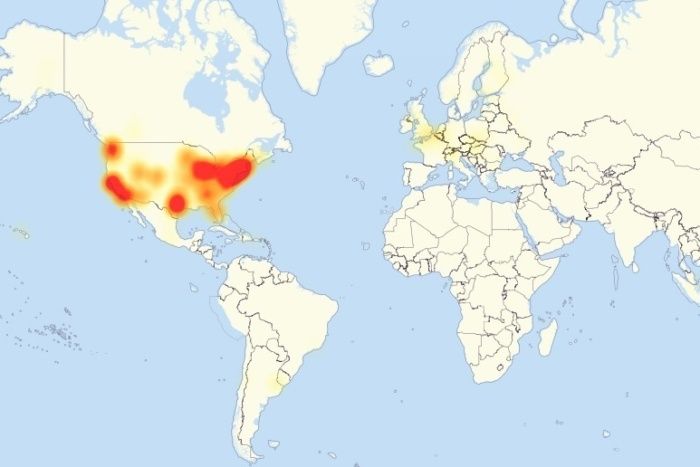
Chinese firm admits its hacked products were behind Friday’s massive DDOS attack
Posted by Roman Mednitzer in categories: cybercrime/malcode, internet
A Chinese electronics component manufacturer says its products inadvertently played a role in a massive cyberattack that disrupted major internet sites in the U.S. on Friday.
Hangzhou Xiongmai Technology, a vendor behind DVRs and internet-connected cameras, said on Sunday that security vulnerabilities involving weak default passwords in its products were partly to blame.
According to security researchers, malware known as Mirai has been taking advantage of these vulnerabilities by infecting the devices and using them to launch huge distributed denial-of service attacks, including Friday’s outage.
Oct 15, 2016
Teen claims he makes $5K a WEEK illegally buying credit card details
Posted by Karen Hurst in category: cybercrime/malcode
No job, no money techie = no problem because you have the Dark Web.
‘New Zealand Wolf of Wall Street’, 19, makes $5000 a week by using credit card details he fraudulently acquires online. With the stolen money, he lives a life normally reserved for Hollywood movies. (stock)
Oct 13, 2016
DARPA investigating blockchain for nuclear weapons, satellite security
Posted by Karen Hurst in categories: bitcoin, cybercrime/malcode, military
If the Defense Department is looking to implement blockchain, other organizations may quickly follow suit. Blockchain technology helps guarantee that information has a timestamp and recorded whenever any change happens, ensuring data can be trusted in real time. In DARPA’s case, blockchain technology could help track attempted data breaches.
“Whenever weapons are employed … it tends to be a place where data integrity in general is incredibly important,” Booher said. “So nuclear command and control, satellite command and control, command and control in general, [information integrity] is very important.”
In September, DARPA awarded a $1.8 million contract to computer security firm Galois, asking it to verify a specific type of blockchain technology from a company called Guardtime. If the verification goes well, the military could become one of a growing number of industries and institutions using blockchain to help ensure the security of their operations.
Continue reading “DARPA investigating blockchain for nuclear weapons, satellite security” »
Oct 13, 2016
Will Quantum Computers Kill Bitcoin?
Posted by Karen Hurst in categories: bitcoin, cybercrime/malcode, encryption, quantum physics
Since they were first theorized by the physicist Richard Feynman in 1982, quantum computers have promised to bring about a new era of computing. It is only relatively recently that theory has translated into significant real-world advances, with the likes of Google, NASA and the CIA working towards building a quantum computer. Computer scientists are now warning that the arrival of the ultra-powerful machines will cripple current encryption methods and as a result bring a close to the great bitcoin experiment—collapsing the technological foundations that bitcoin is built upon.
“Bitcoin is definitely not quantum computer proof,” Andersen Cheng, co-founder of U.K. cybersecurity firm Post Quantum, tells Newsweek. “Bitcoin will expire the very day the first quantum computer appears.”
The danger quantum computers pose to bitcoin, Cheng explains, is in the cryptography surrounding what is known as the public and private keys—a set of numbers used to facilitate transactions. Users of bitcoin have a public key and a private key. In order to receive bitcoin, the recipient shares the public key with the sender, but in order to spend it they need their private key, which only they know. If somebody else is able to learn the private key, they can spend all the bitcoin.
Oct 11, 2016
Quantum Computing Could Cripple Encryption; Bitcoin’s Role
Posted by Karen Hurst in categories: bitcoin, business, cybercrime/malcode, encryption, government, quantum physics
Earlier this week, Canada’s electronic spy agency the Communications Security Establishment warned government agencies and businesses against quantum mechanics, which could cripple the majority of encryption methods implemented by leading corporations and agencies globally.
Governments and private companies employ a variety of cryptographic security systems and protocols to protect and store important data. Amongst these encryption methods, the most popular system is public key cryptography (PKC), which can be integrated onto a wide range of software, platforms, and applications to encrypt data.
The Communications Security Establishment and its chief Greta Bossenmaier believes that quantum computing is technically capable of targeting PKC-based encryption methods, making data vulnerable to security breaches and hacking attempts from foreign state spies and anonymous hacking groups.
Continue reading “Quantum Computing Could Cripple Encryption; Bitcoin’s Role” »
Oct 10, 2016
Commission plans cybersecurity rules for internet-connected machines
Posted by Roman Mednitzer in categories: cybercrime/malcode, food, internet, law, policy, transportation
The European Commission is getting ready to propose new legislation to protect machines from cybersecurity breaches, signalling the executive’s growing interest in encouraging traditional European manufacturers to build more devices that are connected to the internet.
A new plan to overhaul EU telecoms law, which digital policy chiefs Günther Oettinger and Andrus Ansip presented three weeks ago, aims to speed up internet connections to meet the needs of big industries like car manufacturing and agriculture as they gradually use more internet functions.
But that transition to more and faster internet connections has caused many companies to worry that new products and industrial tools that rely on the internet will be more vulnerable to attacks from hackers.
Continue reading “Commission plans cybersecurity rules for internet-connected machines” »
Oct 8, 2016
Artificial intelligence-powered malware is coming, and it’s going to be terrifying
Posted by Shane Hinshaw in categories: cybercrime/malcode, robotics/AI
Smart viruses holding hospital equipment to ransom. Malware that impersonates people you know. Data-altering software that can destroy corporations. Get ready.