Fermi paradox the potentially extreme danger of mirror life.
My Patreon Page:
https://www.patreon.com/johnmichaelgodier.
My Event Horizon Channel:
https://www.youtube.com/eventhorizonshow.
Papers.
Fermi paradox the potentially extreme danger of mirror life.
My Patreon Page:
https://www.patreon.com/johnmichaelgodier.
My Event Horizon Channel:
https://www.youtube.com/eventhorizonshow.
Papers.
Subscribe: https://goo.gl/r5jd1F
Some call it The Great Silence, others The Fermi Paradox.
For the last 60 years, we’ve had our eyes and ears glued to the cosmos looking and listening for some sign letting us know we’re not all alone in the galaxy. And the more we discover, the harder it is to believe we’re the only ones.
Think about this for a moment; there’s around 2 trillion [2,000,000,000,000 galaxies] galaxies in the observable universe. Each one of those galaxies have on average 100 million stars. Some supergiants have one hundred trillion stars, and our Milky Way Galaxy has between 100 to 400 billion stars alone. It is likely that there’s at least this many planets floating around all those stars, and complex planetary systems that may resemble our own Solar System.
It brings us to the big question: where is everyone, and why haven’t we been contacted by an extra-terrestrial civilization from even inside our own galaxy? There should be many advanced civilizations out there, and we should have heard something from someone by now.
There are quite a few possible explanations for the ‘Great Silence’, and some researchers think they may have found some answers to this so-called paradox.
The Fermi Paradox asks why, in a vast and ancient universe, we see no signs of alien life. In this episode, we explore five explanations that make sense—and seven popular ones that, despite sounding good, fall flat under closer scrutiny.
Join this channel to get access to perks:
/ @isaacarthursfia.
Visit our Website: http://www.isaacarthur.net.
Join Nebula: https://go.nebula.tv/isaacarthur.
Support us on Patreon: / isaacarthur.
Support us on Subscribestar: https://www.subscribestar.com/isaac-a… Group: / 1,583,992,725,237,264 Reddit:
/ isaacarthur Twitter:
/ isaac_a_arthur on Twitter and RT our future content. SFIA Discord Server:
/ discord Credits: 5 Fermi Paradox Explanations I Love, 7 That Fall Flat Episode 502 / 721; May 31, 2025 Written, Produced & Narrated by: Isaac Arthur Graphics: Ken York YD Visual Select imagery/video supplied by Getty Images Music Courtesy of Epidemic Sound http://epidemicsound.com/creator 0:00 Intro 1:11 Space Is Too Big 4:46 Rare Earth 6:35 Aliens Signals Just Can’t Be Heard 10:09 Humans Are Boring 11:36 Dark Forest Theory 14:14 Interdiction Bubble Civilizations 16:49 Hermit Hypothesis 19:18 Aestivation Hypothesis and Extragalactic Migration 21:10 Transcendance, Ascension, and Extra-Universe Migration 22:33 Infinite Miniaturization 23:33 Berserkers & Zombie AI 24:53 Aliens Common But Unrecognizable 26:08 Simulation Hypothesis.
Facebook Group: / 1583992725237264
Reddit: / isaacarthur.
Twitter: / isaac_a_arthur on Twitter and RT our future content.
SFIA Discord Server: / discord.
Credits:
5 Fermi Paradox Explanations I Love, 7 That Fall Flat.
Episode 502 / 721; May 31, 2025
Written, Produced & Narrated by: Isaac Arthur.
Graphics: Ken York YD Visual.
Select imagery/video supplied by Getty Images.
Music Courtesy of Epidemic Sound http://epidemicsound.com/creator.
0:00 Intro.
1:11 Space Is Too Big.
4:46 Rare Earth.
6:35 Aliens Signals Just Can’t Be Heard.
10:09 Humans Are Boring.
11:36 Dark Forest Theory.
14:14 Interdiction Bubble Civilizations.
16:49 Hermit Hypothesis.
19:18 Aestivation Hypothesis and Extragalactic Migration.
21:10 Transcendance, Ascension, and Extra-Universe Migration.
22:33 Infinite Miniaturization.
23:33 Berserkers & Zombie AI
24:53 Aliens Common But Unrecognizable.
26:08 Simulation Hypothesis


Although cancer is a common cause of death in domestic cats, little is known about the range of cancer genes in cat tumors, and how this range might compare with the oncogenome in people.
Now, researchers in Science have sequenced cancer genes in 493 samples from 13 different types of feline cancer and matched healthy control tissue, gaining a clearer picture of the cat oncogenome and comparing the genes to known cancer-causing mutations in humans.
Cancer is a common cause of morbidity and mortality in domestic cats. Because the mutational landscape of domestic cat tumors remains uncharacterized, we performed targeted sequencing of 493 feline tumor–normal tissue pairs from 13 tumor types, focusing on the feline orthologs of ~1000 human cancer genes. TP53 was the most frequently mutated gene, and the most recurrent copy number alterations were loss of PTEN or FAS or gain of MYC. By identifying 31 driver genes, mutational signatures, viral sequences, and tumor-predisposing germline variants, our study provides insight into the domestic cat oncogenome. We demonstrate key similarities with the human oncogenome, confirming the cat as a valuable model for comparative studies, and identify potentially actionable mutations, aligning with a “One Medicine” approach.

Will artificial intelligence ever be able to reason, learn, and solve problems at levels comparable to humans? Experts at the University of California San Diego believe the answer is yes—and that such artificial general intelligence has already arrived. This debate is tackled by four faculty members spanning humanities, social sciences, and data science in a recently published Comment invited by Nature.
Computer scientist Alan Turing first posed this question in his landmark 1950 paper, though he didn’t use the term artificial general intelligence (AGI). His “imitation game,” now known as the Turing Test, asked whether a machine could pass as human in text-based conversation with humans. Seventy-five years later, that future is here.
Over the past year, Associate Professor of Philosophy Eddy Keming Chen, Professor of Artificial Intelligence, Data Science and Computer Science Mikhail Belkin, Associate Professor of Linguistics and Computer Science Leon Bergen, and Professor of Data Science, Philosophy and Policy David Danks engaged in extensive dialogue on this question. These discussions happened as another set of researchers at UC San Diego found in March 2025 that the large language model GPT-4.5 was judged to be human 73% of the time in a Turing test—much more often than actual humans.

This local biotech says it has found a way to trick cancer cells into destroying themselves with its molecular glue. Now it’s putting that claim to the test. After attracting global attention from researchers and billions of dollars from Big Pharma, Neomorph announced that it has begun its first clinical trial. The molecular glue aims to treat a form of kidney cancer.
The first trial will dose one patient with the molecular glue, NEO-811, to treat clear cell renal cell carcinoma, the most common kind of kidney cancer.
In San Diego County, roughly 500 people are diagnosed with kidney cancer each year—that’s more than one new case every day, according to the California Cancer Registry. Among residents 65 and older, the rate jumps to more than four times higher than the overall population: 2,000 San Diegan’s over 65 are diagnosed with a form of kidney cancer each year.
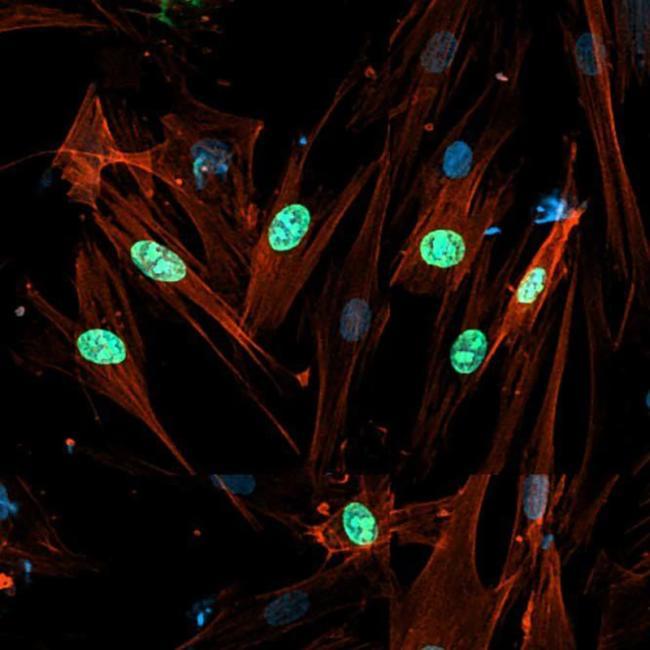
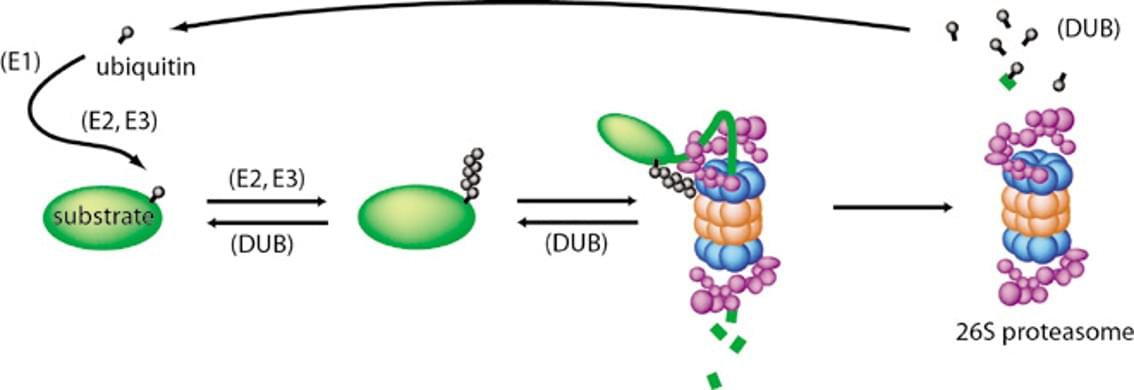

One of the most-viewed PNAS articles in the last week is “Lipid nanoparticle GM-CSF replacement for autoimmune pulmonary alveolar proteinosis.” Explore the article here: https://ow.ly/QMWH50Yl87H
For more trending articles, visit https://ow.ly/pmKX50Yl87I.
Granulocyte–macrophage colony-stimulating factor (GM-CSF) deficiency drives autoimmune pulmonary alveolar proteinosis (aPAP), a disease characterized by impaired macrophage-mediated clearance of pulmonary surfactants. Clinical data suggest that inhaled recombinant GM-CSF reduces symptoms in aPAP patients, providing a rationale for mRNA-based GM-CSF replacement therapies. However, these require effective mRNA delivery after nebulization. Here, we report the iterative in vivo design of a lipid nanoparticle, named nebulized lung delivery 2 (NLD2), that efficiently delivers mRNA after nebulization. NLD2 carrying GM-CSF mRNA transfected alveolar macrophages in vivo, leading to interleukin-10 pathway activation and subsequent surfactant lipoprotein clearance. In a preclinical disease model of aPAP, GM-CSF mRNA delivery reduced surfactant protein thickness more than recombinant GM-CSF. These data support continued exploration of nebulized lipid nanoparticle therapies for aPAP.