UK police urges users to switch on two-factor authentication.


As the amount of data stored in devices and shared over the internet continuously increases, computer scientists worldwide are trying to devise new approaches to secure communications and protect sensitive information. Some of the most well-established and valuable approaches are cryptographic techniques, which essentially encrypt (i.e., transform) data and texts exchanged between two or more parties, so that only senders and receivers can view it in its original form.
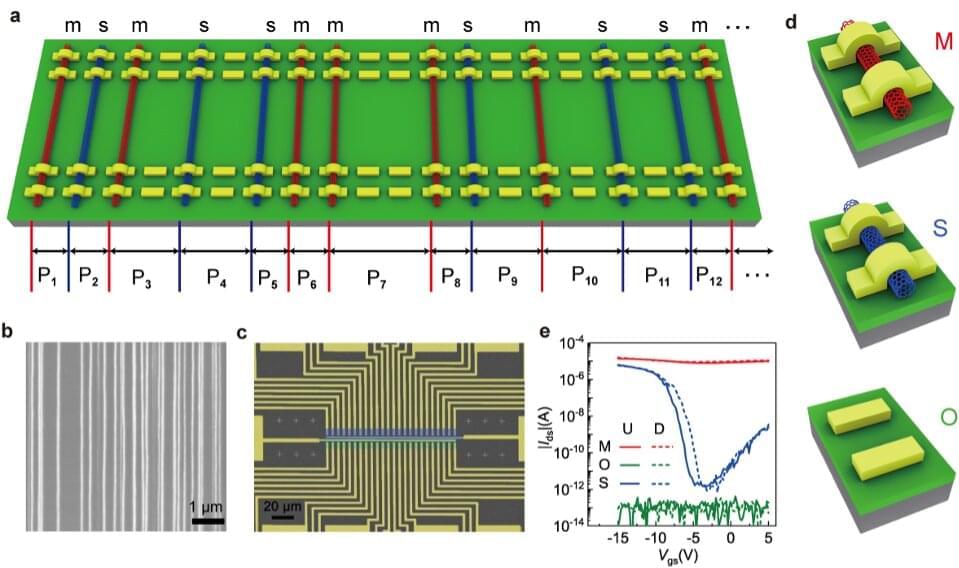
Physical unclonable functions (PUFs), devices that exploit “random imperfections” unavoidably introduced during the manufacturing of devices to give physical entities unique “fingerprints” (i.e., trust anchors). In recent years, these devices have proved to be particularly valuable for creating cryptographic keys, which are instantly erased as soon as they are used.
Researchers at Peking University and Jihua Laboratory have recently introduced a new system to generate cryptographic primitives, consisting of two identical PUFs based on aligned carbon nanotube (CNT) arrays. This system, introduced in a paper published in Nature Electronics, could help to secure communications more reliably, overcoming some of the vulnerabilities of previously proposed PUF devices.
Why we need AI to compete against each other. Does a Great Filter Stop all Alien Civilizations at some point? Are we Doomed if We Find Life in Our Solar System?
David Brin is a scientist, speaker, technical consultant and world-known author. His novels have been New York Times Bestsellers, winning multiple Hugo, Nebula and other awards.
A 1998 movie, directed by Kevin Costner, was loosely based on his book The Postman.
His Ph.D in Physics from UCSD — followed a masters in optics and an undergraduate degree in astrophysics from Caltech. He was a postdoctoral fellow at the California Space Institute and the Jet Propulsion Laboratory.
Brin serves on advisory committees dealing with subjects as diverse as national defense and homeland security, astronomy and space exploration, SETI and nanotechnology, future/prediction and philanthropy. He has served since 2010 on the council of external advisers for NASA’s Innovative and Advanced Concepts group (NIAC), which supports the most inventive and potentially ground-breaking new endeavors.
https://www.davidbrin.com/books.html.
https://twitter.com/DavidBrin.
https://www.newsweek.com/soon-humanity-wont-alone-universe-opinion-1717446
Youtube Membership: https://www.youtube.com/channel/UCz3qvETKooktNgCvvheuQDw/join.
Podcast: https://anchor.fm/john-michael-godier/subscribe.
Apple: https://apple.co/3CS7rjT
More JMG
https://www.youtube.com/c/JohnMichaelGodier.
Want to support the channel?
US Rep Jason Crow, of the US House Intelligence Committee, warned that bio-weapons are being made that use a target’s DNA to only kill that person at a security forum on Friday.
An Israeli security researcher has demonstrated a novel attack against air-gapped systems by leveraging the SATA cables inside computers as a wireless antenna to emanate data via radio signals.


Surveillance, Preparedness & Health Security In Critical Disease Emergencies — Dr. Rosamund Lewis, MD, Head, WHO Smallpox Secretariat, Technical Lead for Monkeypox.
Dr. Rosamund Lewis, MD, is Head, WHO Smallpox Secretariat, Emerging Diseases and Zoonoses Unit, World Health Emergencies Programme, at the World Health Organization in Geneva, Switzerland, leading on emergency preparedness and advising on health security for the agency in this very critical domain, including as technical lead for Monkeypox. She also holds an appointment as Adjunct Professor in the School of Epidemiology and Public Health, University of Ottawa.
Previous to this role, Dr. Lewis joined the WHO COVID-19 response team as the health sciences lead for management of infodemics.
A public health physician with an early career in family and emergency medicine, Dr. Lewis has served the WHO, the Government of Canada, Ottawa Public Health and other agencies at global, national and municipal levels in emergency preparedness, health security, disease surveillance and response, offering country support for a range of immunization and disease control programs.
Dr. Lewis has served other roles focused on field epidemiology in emergency settings with organizations like Doctors Without Borders, and new vaccines and health systems development with the Global Vaccine Alliance (GAVI).

Security researchers have detected a massive campaign that scanned close to 1.6 million WordPress sites for the presence of a vulnerable plugin that allows uploading files without authentication.
The attackers are targeting the Kaswara Modern WPBakery Page Builder, which has been abandoned by its author before receiving a patch for a critical severity flaw tracked as CVE-2021–24284.
The vulnerability would allow an unauthenticated attacker to inject malicious Javascript to sites using any version of the plugin and perform actions like uploading and deleting files, which could lead to complete takeover of the site.
