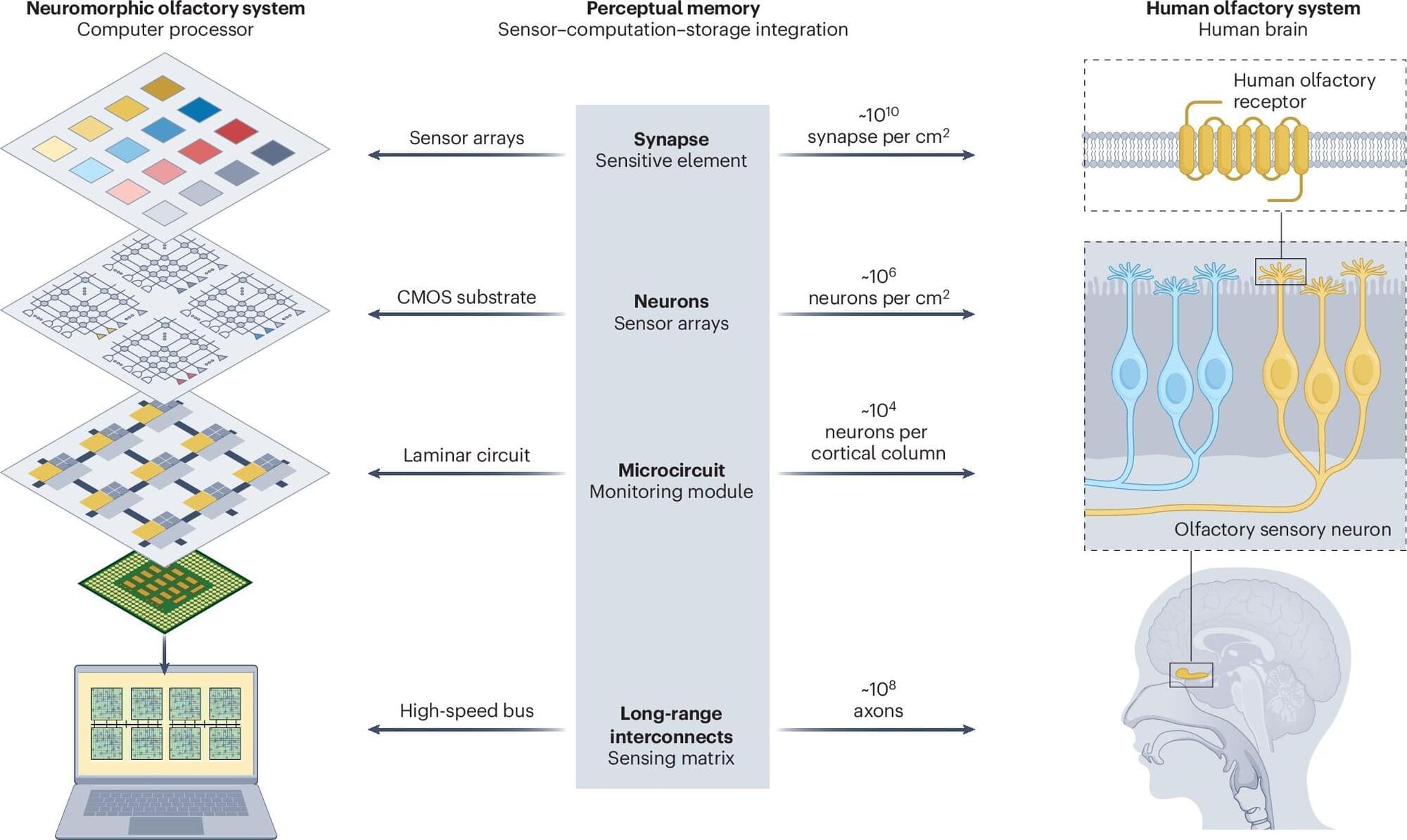
After years of trying, the electronic nose is finally making major progress in sensing smells, almost as well as its human counterpart. That is the conclusion of a scientific review into the development of neuromorphic olfactory perception chips (NOPCs), published in the journal Nature Reviews Electrical Engineering.
Evolution has perfected the human nose over millions of years. This powerful sense organ, while not the best in the animal kingdom, can still detect around a trillion smells. The quest to develop electronic noses with human nose-like abilities for applications like security, robotics, and medical diagnostics has proved notoriously difficult. So scientists have increasingly been turning to neuromorphic computing, which involves designing software and hardware that mimics the structure and function of the human nose.
In this review, a team of scientists from China highlights some of the key advances in developing olfactory sensing chips. The paper focuses heavily on gas sensors because they are key components of the electronic nose system. They must physically detect odor molecules and convert them into electrical signals.