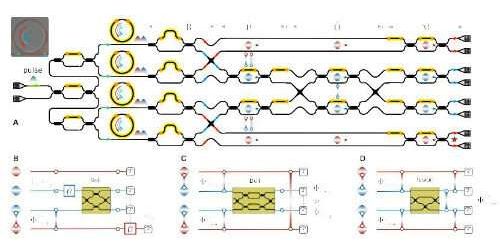
As access to the internet grows, so do the risks associated with being online. Cybersecurity threats are on the rise as data hackers find new ways to breach through firewalls. Earlier this year bad actors were able to gain access to the administrative serves of India’s largest nuclear power plant with a simple phishing email.
The government want to increase its cyber might to ward off such hazards but experts feel some of its policies might do the exact opposite.
2020 will be a busy year for India with the 5G spectrum auction still pending, Personal Data Protection Bill under discussion, and the deadline for social.