Hackers using a “complex and powerful” malware loader with the ultimate objective of deploying cryptocurrency miners on compromised systems.
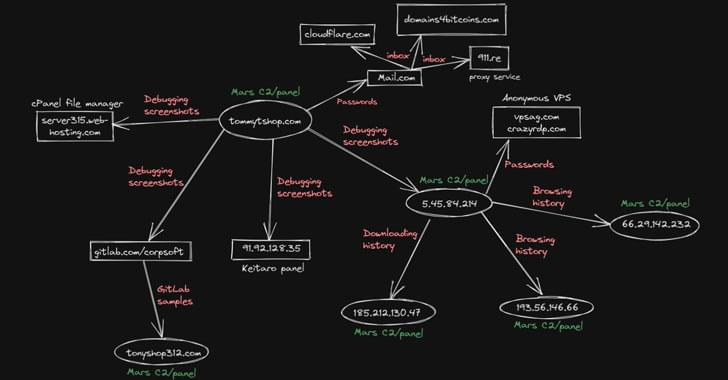
Researchers have uncovered a new malware campaign spreading Mars info-stealer via Google ads.

WASHINGTON — SpiderOak Mission Systems announced March 29 it won a contract from Lockheed Martin Space for its cybersecurity software.
The contract allows Lockheed Martin to use SpiderOak’s OrbitSecure software. “This is commercial technology that was developed for terrestrial applications and has been repurposed for the space business, specifically for low Earth orbit,” SpiderOak chairman Charles Beames told SpaceNews.
Beames said he could not disclose the value of the contract with Lockheed Martin. “The goal is to make OrbitSecure available to Lockheed Martin customers as part of an offering to provide an extra level of cybersecurity,” he said.
KELVIN OGBA DAFIAGHOR joins us all the way from Nigeria to attend #GISECGlobal 2022. He is the CEO of the Ogba Educational Clinic and he decided to visit GISEC to network with cybersecurity professionals from all over the world, as well as tech giants exhibiting at the show. It’s been an absolute pleasure having you with us, Kelvin, see you in 2023! 🤩.

Ernesto Di Maio is severely allergic to the yeast in leavened foods. “I have to go somewhere and hide because I will be fully covered with bumps and bubbles on the whole body,” he says. “It’s really brutal.”
Di Maio is a materials scientist at the University of Naples Federico II where he studies the formation of bubbles in polymers like polyurethane. He’s had to swear off bread and pizza, which can make outings in Italy a touch awkward. “It’s quite hard in Naples not to eat pizza,” he explains. “People would say, ‘Don’t you like pizza? Why are you having pasta? That’s strange.’”
So Di Maio put Iaccarino and another graduate student, Pietro Avallone, to work on a project to make pizza dough without yeast. The results of this scientific and culinary experiment are published in Tuesday’s edition of Physics of Fluids. Di Maio pulled in another colleague: chemical engineer Rossana Pasquino who studies the flow of materials, everything from toothpaste to ketchup to plastics. “Pizza [dough] is a funny material,” she explains, “because it flows, but it has to be also like rubber. It has to be elastic enough [when it’s cooked] to be perfect when you eat it.” — I had to post this because I love Pizza.
Bread geeks, take note! The new technique, developed in a lab in Naples, involves the smart application of materials science and physics to make airy, bubbly dough without fermentation.

You’ve probably received this message already — just don’t open it. Details:
Facebook Messenger users have been told to ignore a four-letter message that could lead to disastrous financial consequences or stolen personal information.
Scammers use the instant messaging platform to send out a four-word “look what I found …” message, and a link from compromised accounts. These message also include emojis as well, 7News reports.
If interacted with, the link takes the user to a site where they’re asked to enter their Facebook log in details. This allows the scammer to steal sensitive information from the user’s profile, or install malware on their phone or computer.



A new malware strain that can survive operating system reinstalls was spotted last year secretly hiding on a computer, according to the antivirus provider Kaspersky.
The company discovered the Windows-based malware last spring running on a single computer. How the malicious code infected the system remains unclear. But the malware was designed to operate on the computer’s UEFI firmware, which helps boot up the system.
The malware, dubbed MoonBounce, is especially scary because it installs itself on the motherboard’s SPI flash memory, instead of the computer’s storage drive. Hence, the malware can persist even if you reinstall the computer’s OS or swap out the storage.

“The investigation into the recent cyber event on the KA-SAT European network continues in partnership with law enforcement, government partners and Viasat’s third-party cybersecurity firm,” Viasat said in a statement March 11. “We currently believe this was a deliberate, isolated and external cyber event.”