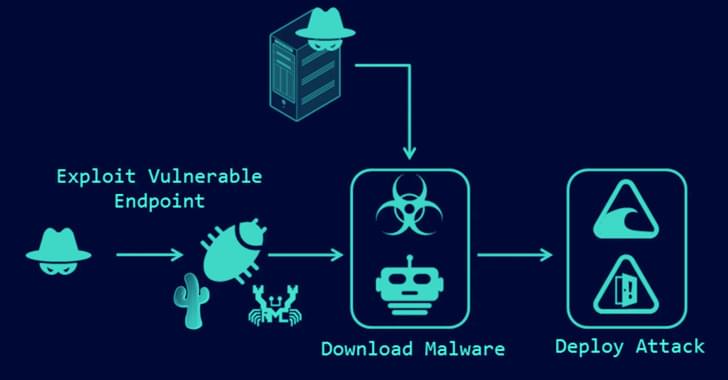
The travel and tourism sector has become a prime focus for cyberattacks in recent times, resulting in ransomware incidents arising from data breaches. Against this backdrop, cybersecurity concerns within the industry have escalated with a 4 pc year-on-year (YoY) rise in 2022, reflecting the prevailing sentiment, says GlobalData, a leading data and analytics company.
In its report, Company Filing Analytics Database, GlobalData says that sentiment for airlines, travel services, and lodging rose by 6 pc, 4 pc, and 1 pc, respectively, in 2022 over 2021.
“Companies are consistently working on information and network security projects to set up a reliable technical protection and security management mechanism to ensure customer security and prevent data leakage. A severe data security incident can lead to operational disturbances and cause significant financial damage to the business,” says Misa Singh, Business Fundamentals Analyst at GlobalData.