AI has just made its next big move! The Humane AI Wearable made its debut on a TED talk. Its coming after iPhones and Android smartphones!
Category: mobile phones – Page 83
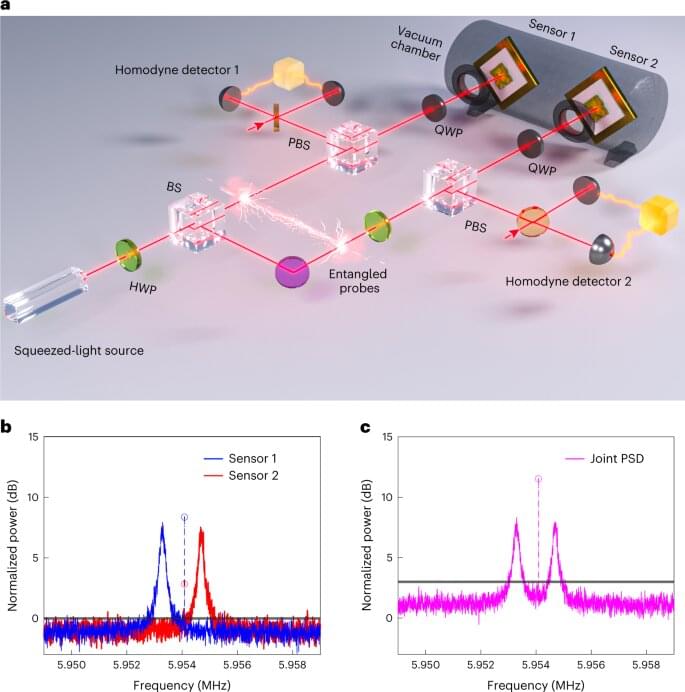
Quantum entanglement could make accelerometers and dark matter sensors more accurate
The “spooky action at a distance” that once unnerved Einstein may be on its way to being as pedestrian as the gyroscopes that currently measure acceleration in smartphones.
Quantum entanglement significantly improves the precision of sensors that can be used to navigate without GPS, according to a new study in Nature Photonics.
“By exploiting entanglement, we improve both measurement sensitivity and how quickly we can make the measurement,” said Zheshen Zhang, associate professor of electrical and computer engineering at the University of Michigan and co-corresponding author of the study. The experiments were done at the University of Arizona, where Zhang was working at the time.



Panic at Google: Samsung considers dumping search for Bing and ChatGPT
The New York Times has a big piece detailing Google’s “shock” and “panic” when Samsung recently floated the idea of switching its smartphones from Google Search to Bing. After being the butt of jokes for years, Bing has been seen as a rising threat to Google thanks to Microsoft’s deal with OpenAI and the integration of the red-hot ChatGPT generative AI. Now, according to the report, one of Android’s biggest manufacturers is threatening to switch its new phones away from Google Search.
Of course, preinstalled search deals are more about cash than quality. Google pays billions every year to be the default search engine on popular products with deals framed as either “revenue sharing” or “traffic acquisition fees.” Google reportedly pays as much as $3.5 billion per year to be the default search on Samsung phones, while it pays Apple $20 billion per year to be the default search on iOS and macOS. The report notes that the Samsung/Google search contract “is under negotiation, and Samsung could stick with Google.”


How to put ChatGPT on Galaxy Watch, Pixel Watch, Wear OS
It’s available on phones and now watches? That’s actually nice though I hope they make it battery efficient. The Pixel watch for example already has issues with battery life. I’m the future will there be a small AI server in our bodies in microchips or a network of nanobots?
ChatGPT is all the rage these days, but did you know you can get it on your watch? Here’s how to install it on a Galaxy Watch, Pixel Watch, and other Wear OS watches.
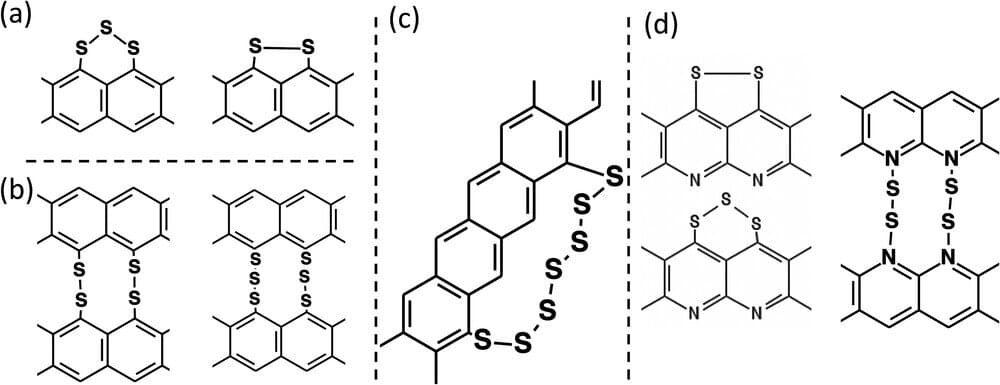
Research provides new insight into quantum effects in lithium sulfur batteries
Lithium-ion batteries power our lives.
Because they are lightweight, have high energy density and are rechargeable, the batteries power many products, from laptops and cell phones to electric cars and toothbrushes.
However, current lithium-ion batteries have reached the limit of how much energy they can store. That has researchers looking for more powerful and cheaper alternatives.
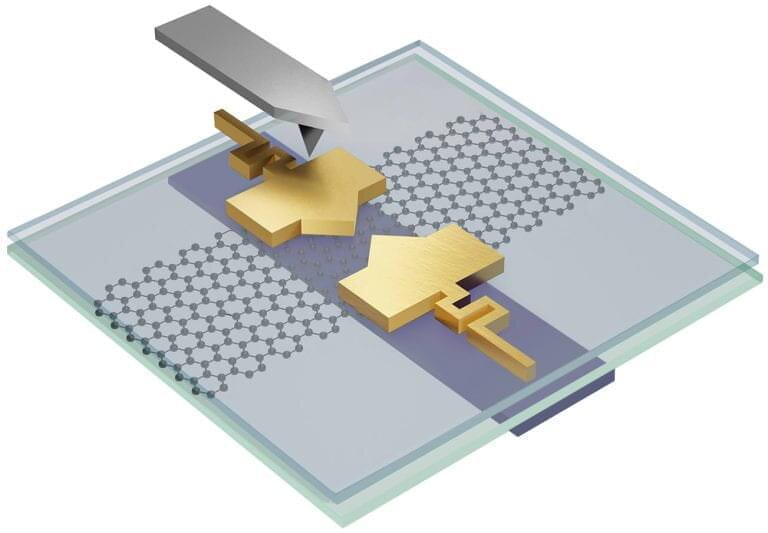
Physicists discover first transformable nanoscale electronic devices
The nanoscale electronic parts in devices like smartphones are solid, static objects that once designed and built cannot transform into anything else. But University of California, Irvine physicists have reported the discovery of nanoscale devices that can transform into many different shapes and sizes even though they exist in solid states.
It’s a finding that could fundamentally change the nature of electronic devices, as well as the way scientists research atomic-scale quantum materials. The study is published in Science Advances.
“What we discovered is that for a particular set of materials, you can make nanoscale electronic devices that aren’t stuck together,” said Javier Sanchez-Yamagishi, an assistant professor of physics & astronomy whose lab performed the new research. “The parts can move, and so that allows us to modify the size and shape of a device after it’s been made.”
