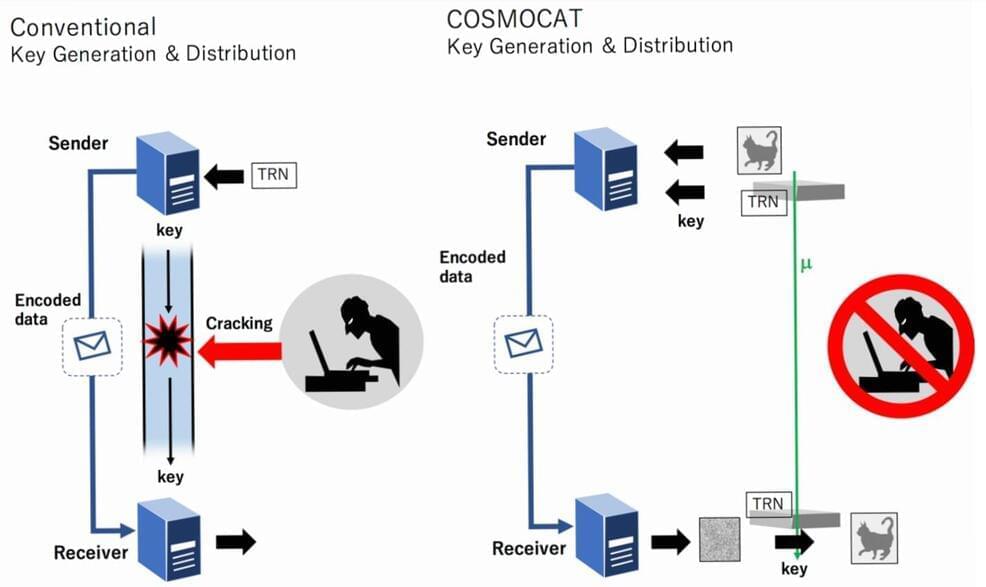
State-of-the-art methods of information security are likely to be compromised by emerging technologies such as quantum computers. One of the reasons they are vulnerable is that both encrypted messages and the keys to decrypt them must be sent from sender to receiver.
A new method—called COSMOCAT—is proposed and demonstrated, which removes the need to send a decryption key since cosmic rays transport it for us, meaning that even if messages are intercepted, they could not be read using any theorized approach. COSMOCAT could be useful in localized various bandwidth applications, as there are limitations to the effective distance between sender and receiver.
In the field of information communication technology, there is a perpetual arms race to find ever more secure ways to transfer data, and ever more sophisticated ways to break them. Even the first modern computers were essentially code-breaking machines used by the U.S. and European Allies during World War II. And this race is about to enter a new regime with the advent of quantum computers, capable of breaking current forms of security with ease. Even security methods which use quantum computers themselves might be susceptible to other quantum attacks.