Quantum computers have the potential to outperform conventional computers on some tasks, including complex optimization problems. However, quantum computers are also vulnerable to noise, which can lead to computational errors.
Engineers have been trying to devise fault-tolerant quantum computing approaches that could be more resistant to noise and could thus be scaled up more robustly. One common approach to attain fault-tolerance is the preparation of magic states, which introduce so-called non-Clifford gates.
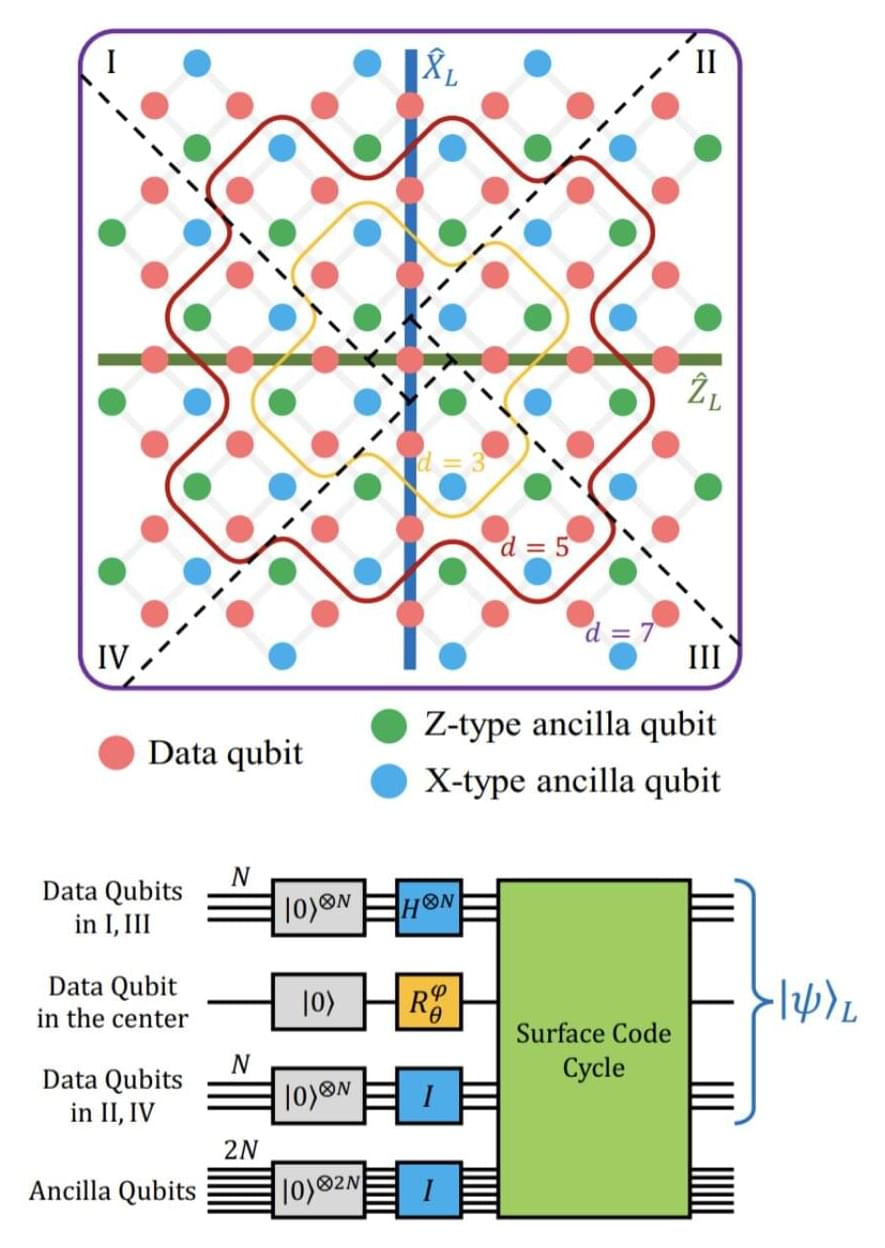
Researchers at University of Science and Technology of China, the Henan Key Laboratory of Quantum Information and Cryptography and the Hefei National Laboratory recently demonstrated the preparation of a logical magic state with fidelity beyond the distillation threshold on a superconducting quantum processor. Their paper, published in Physical Review Letters, outlines a viable and effective strategy to generate high-fidelity logical magic states, an approach to realize fault-tolerant quantum computing.